What is steganography?
Steganography is when you hide text or something inside something in an image. To the naked eye, the picture will just look like a picture, but the image can hold secrets. In this tutorial we will be hiding a Monero seed into an image.
First we will encrypt the seed using GPG. That way even if the image gets in the wrong hands they will not be able to steal your Monero. To access the seed the user will need to decrypt it using their private key.
It is important to use a super secure password when choosing a password for your key. Text or images can also be hidden in audio files.
You can learn more about GPG or PGP by reading this article about the basics of GPG.
Encrypting the seed or keys with GPG

The first step is create a new wallet and save the seed or the keys to a file named “seed.txt”. This guide assumes you already have GPG installed and a key pair. Use the command below to encrypt the file seed.txt.

The “-a” will make the results asci friendly, the “-r” flag is the recipients and lastly the “-e” flag will encrypt the text file.
The command will generate a file named “seed.txt.asc”. You should copy the file’s contents to your clipboard. You will need it later to embed into the image.
Downloading Silent Eye
Download Silent Eye from this site. Silent Eye is a handy tool that allows you to easily embed text into a image. The application is open sourced.
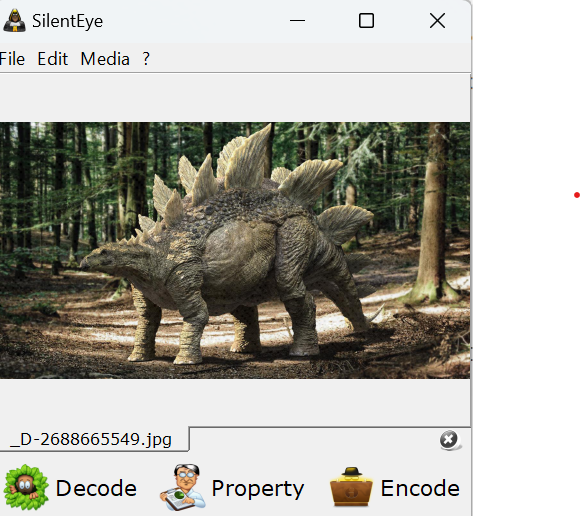
First step is to open the image file that you want to embed your seed or key in. Next Click the Encode button. A window like the image below should show up.
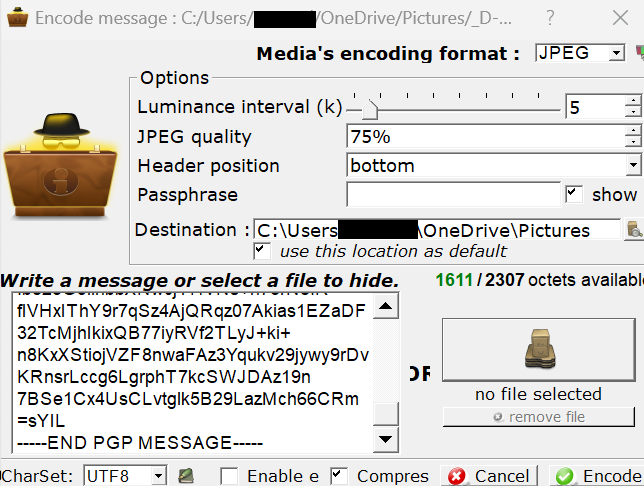
Next edit the destination to where you want the file saved to. After doing that paste the contents of seed.txt.asc in the message field.
Now remove the passphrase or if you want extra security put a password. Lastly click the “encode” button.
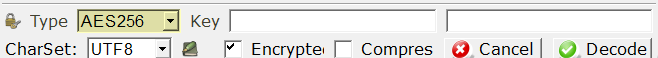
If you do not want to use GPG, you can enter a key in the field if you want to use AES instead of GPG.
Congrats you have now safety hid your seed in an image!
Decoding the seed from the image!
Once again, import the file that has your seed or keys. Like the image below:
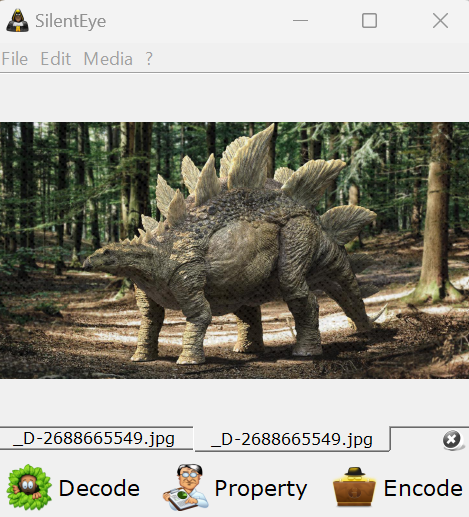
Now click the “Decode” button. The screen will look like the image below.
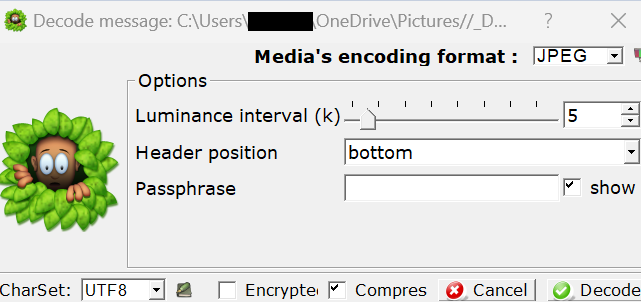
Before you click the “Decode” button remove the password field. If you decided to use a password for extra protection type in the password. Lastly click the “Decode” button. After clicking the “Decode” button a new window will pop up like the image below.
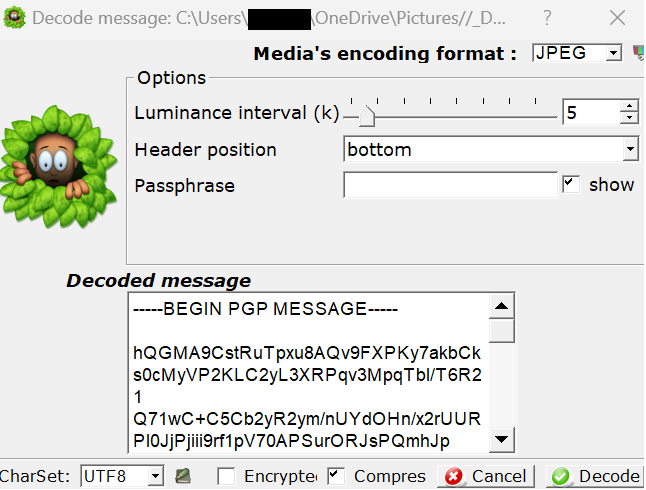
Notice that the “Decoded message” field has the GPG encrypted seed. Now copy the “Decoded message” to your clipboard and save it to a file which we will now use GPG to decrypt the seed.
Use the following command to decrypt the encrypted seed. The “-r” flag for the recipient. The “-a” is to make sure the output is asci. Lastly the “-d” is where you put the file where you file where you saved the encrypted seed.

The output should look like the image below. You will need to enter you private key’s password to be able to successfully decrypt the keys. Note: that this is a random key. It has no Monero in it.
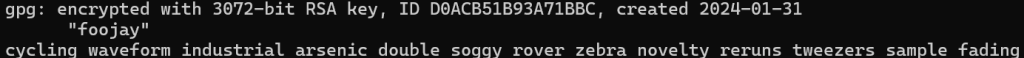
The seed is the text on the last line of the image.
Encrypt you seed with StegHide
StegHide is another handy tool that can be used to hide information in files. This tool has versions for Linux and Windows systems. StegHide can be downloaded here. First step is to unzip the file after downloading.
First step is to open a terminal and use the “cd” command to change the directory where the StegHide file is. Follow the same instructions on encrypting the seed with your GPG key that was shown earlier in this tutorial.
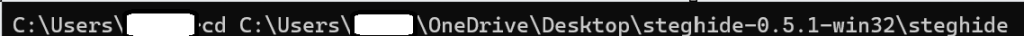
To make things easy I copy and pasted the Dino image into the same directory where StegHIde is. I did the same to a text file that includes the seed that is encrypted with my GPG key.
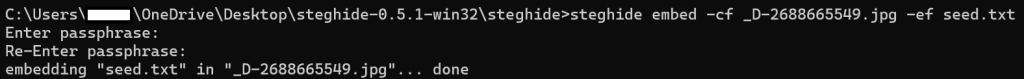
As seen in the image above I used the following command to hide “seed.txt” into the JPG image.
steghide embed -cf _D-2688665549.jpg -ef seed.txtExtracting the text from an image!
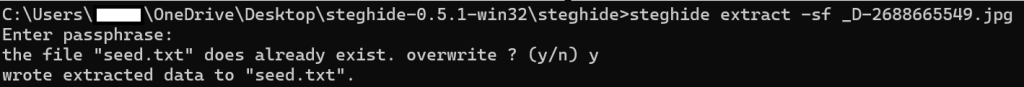
As seen in the image above we extracted the file from the JPG image, “_D-2688665549.jpg”. The command used to extract the text can be seen below.
steghide>steghide extract -sf _D-2688665549.jpgIf you decided to enter a password, please enter the password. The extracted seed will be saved in the file named “seed.txt”.
If you want to extract the seed in a different named file use the following command with the “-xf” flag which will save the extracted seed in a file named “test.txt”.
extract -sf _D-2688665549.jpg -xf test.txtLazy man’s Steganography!

This part of the tutorial requires a Linux system. First encrypt your seed with your GPG key, copy the contents to your clipboard. The following command will add your encrypted seed to the end of a PNG file.
echo "_YOUR_ENCRYPTED_SEED_" >> boom.pngFirst use the GPG command explained earlier to encrypt your seed and save it to your clipboard. Please replace the “_YOUR_ENCRYPTED_SEED_” line with your GPG encrypted seed that you saved in your clipboard. The “>>” part will add your encrypted seed to the end of the file named “boom.png”
Viewing the encrypted seed !
Again this part requires you to be using Linux. Run the following command to view your encrypted seed:
cat boom.pngAfter running the command the very last line should have the encrypted seed. Now you can use the already explain method of decrypting the encrypted seed using GPG.
